Part 2: Microsoft Fabric admin - Adding Entra ID groups to workspaces with Semantic Link and Python
Context
This post is a part 2 of the Fabric administration series. The goal of this post is to show you 2 ways to add Microsoft Entra ID security groups in your Fabric workspace:
Using Semantic Link
Using the Power BI REST APIs using a Service Principal in Python
Understanding the problem
Following the scenario from Part 1, after creating the workspaces, the next step is to add Microsoft Entra ID security groups (I'd recommend avoiding adding individual users—trust me, it can turn into a governance mess). Here I thought, ok I have multiple options to do this task such as: Power BI REST API, Python wrapper pbipy library, semantic link in a Fabric notebook, the new Terraform provider for Fabric.
Is it possible to solve with semantic link?
One big advantage of using semantic link in a Fabric notebook is that you don’t have to worry about authentication (you don’t need a Service Principal). I checked the sempy and semantic-link-labs library, if you can add a Microsoft Entra ID security group using the Python library. Here is what I found:
Using the sempy: I didn’t found any function (method) in this Python library to perform this task. But you could call the Power BI / Fabric REST APIs and then just work with the API itself
Using the semantic-link-labs: There is actually a method in this Python library that you could use to add users and also Entra ID security groups (as long as you know the object ID)
Solution 1: using semantic link
Prerequisites:
Using semantic link you don’t need to worry about authentication in Fabric, but for this task our goal is to get the object ID from the Entra ID security group based on the name of the security group. For this reason, we are going to use a Service Principal. If you have another way to get this object ID, so you don’t need the Service Principal. See below the prerequisites before we dive into the solution :)
Create a service principal to use the Fabric / Power BI REST APIs
API permission: after creating the service principal, you should set the API permission to allow getting the object ID from security groups:
You can find the Python notebook below as screenshot:
You can find the Python notebook code in my Github repo:
Github Repo with the Python code
Considerations
I want to highlight the importance to check what the Python function is doing behind scene especially if you find some problems in the way.
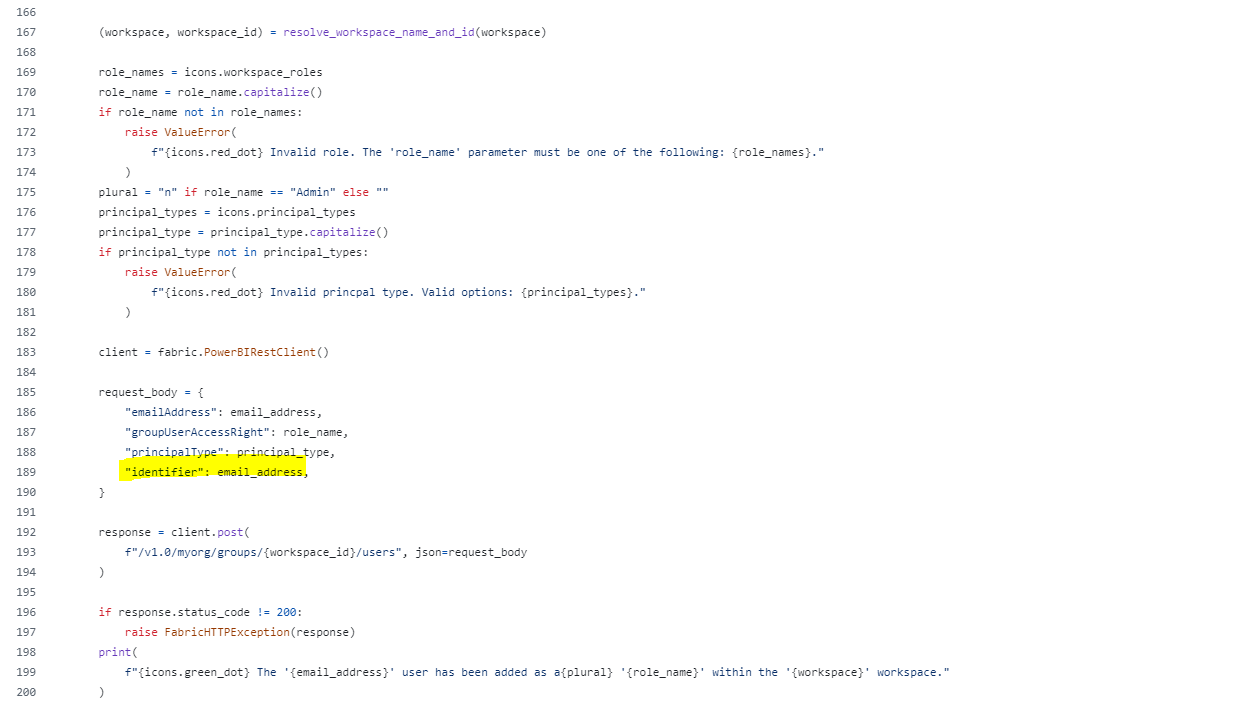
For example, when using the “add_user_to_workspace” method from the semantic-link-labs Python library I encountered some problems especially because you only enter the following parameters:
So, I was asking myself where can I enter the object ID from the security group. When using the Power BI REST API you can enter this value as “identifier” in the body. Here comes the importance to check what is happening behind the hood :) in the code the “identifier” gets the “email_address” in the body for the API call:
Therefore, there is no problem entering the object ID from the security group in the “email_adress” parameter. The Github repo from semantic-link-labs can be found here.
Solution 2: using only REST APIs
The prerequisites for this solution are the same from my first post about Part 1: Microsoft Fabric admin - How to create multiple workspaces using Python.
You can find the Python code below as screenshot:
You can find below the Python code in my Github repo:
Github Repo with the Python code
Last updated on October 26, 2024